How to become a Full Stack Developer in 2025
Learn the step-by-step process to become a full stack developer in the current job market.
Read More
Guiding your path to success
At Provigo Technologies, the leading training institute in Chennai, we believe that every learner has the potential to achieve greatness when guided with the right knowledge and mentorship. As the best software training in Guduvanchery, our mission is to empower students with practical skills through our Full-stack developer course Chennai, Java training with placement, Python training in Chennai, web development course in Chennai, UI/UX course Chennai.
We focus on real-world applications, ensuring every concept you learn can be applied in practical scenarios.
Learn directly from professionals who bring years of expertise and insights from the field.
Small batch sizes and one-on-one guidance to ensure every learner gets the attention they deserve.
Clients
Projects
Hours Of Support
Workers
We provide comprehensive career support services, including resume building, interview preparation, internship opportunities, and personalized mentorship to help you achieve your professional goals.
Our On-Job Support services are designed to help professionals overcome workplace challenges with confidence. Whether you are handling new projects, learning advanced tools, or facing technical issues, our experts provide step-by-step guidance and practical solutions. We ensure you succeed in your role while gaining valuable skills for career growth.
We offer exciting internship opportunities for students and fresh graduates to gain hands-on experience in real-world projects. Our internships provide practical learning, mentorship from industry experts, and skill development that prepares you for a successful career. Join us to explore, learn, and build your future with confidence.
Resume building is a crucial step in shaping your career. A well-crafted resume highlights your skills, strengths, and achievements, making you stand out to employers. Our guidance helps you create professional, structured, and impactful resumes that reflect your true potential and increase your chances of securing opportunities.
Our Interview Preparation program equips candidates with the confidence and skills to excel in job interviews. We provide guidance on common questions, mock interviews, communication techniques, and presentation skills. With expert feedback and practical tips, we help you showcase your strengths effectively and succeed in securing your dream job.
Our Doubt-Solving Sessions are designed to provide personalized support and clarity for every learner. Whether it’s technical concepts, project challenges, or subject-related queries, our experts offer step-by-step explanations and practical solutions. These sessions help students build confidence, strengthen understanding, and achieve better results through guided learning.
Career guidance helps individuals choose the right path by identifying their strengths, interests, and goals. With expert mentoring and personalized advice, we support students and professionals in making informed decisions about education, skills, and careers. Our guidance ensures clarity, confidence, and a roadmap for long-term success.

Start Your Learning Journey Today!
Unlock your potential with our industry-focused training programs. Whether you’re starting fresh or upgrading your skills, our expert trainers, hands-on projects, and personalized mentorship will help you achieve your career goals.
New batches starting soon – don’t miss your chance!
Contact us now and take the first step towards your success.
"Explore our wide range of expertly designed courses to enhance your skills, advance your career, and fuel your passion for learning."

Master advanced JavaScript concepts, from ES6+ features to async programming, and build dynamic web apps.

Learn the core principles of UI/UX design to create intuitive, user-friendly, and visually appealing digital experiences.

Learn .NET from the ground up, building robust, scalable, and high-performance applications with hands-on projects.

Master Python programming and build real-world machine learning applications with ease.

Learn the essentials of Cloud Computing, including services, deployment models, and practical applications in the modern tech world.

Master the core concepts of Data Science, from data analysis and visualization to machine learning and real-world problem-solving.

Learn the essentials of Git, from version control basics to advanced branching, merging, and collaboration workflows used in real-world projects.

Master server-side JavaScript with Node.js, covering asynchronous programming, event-driven architecture, and building fast, scalable applications from scratch.

Learn cloud computing with Microsoft Azure, from deploying web apps and managing databases to implementing scalable, secure, and globally distributed solutions for modern businesses.

Build dynamic and responsive user interfaces with React, a powerful JavaScript library for creating component-based, fast, and interactive web applications.

Develop robust, scalable, and dynamic web applications with Angular, a TypeScript-based framework that offers powerful tools for building interactive, single-page applications with ease.

Store, manage, and retrieve data efficiently with MongoDB, a flexible NoSQL database that uses a document-oriented approach for high performance, scalability, and ease of development.
Web design is the art and science of creating websites that are both attractive and easy to use. It involves planning layouts, choosing colors, fonts, and images, and ensuring that the site is responsive across different devices.
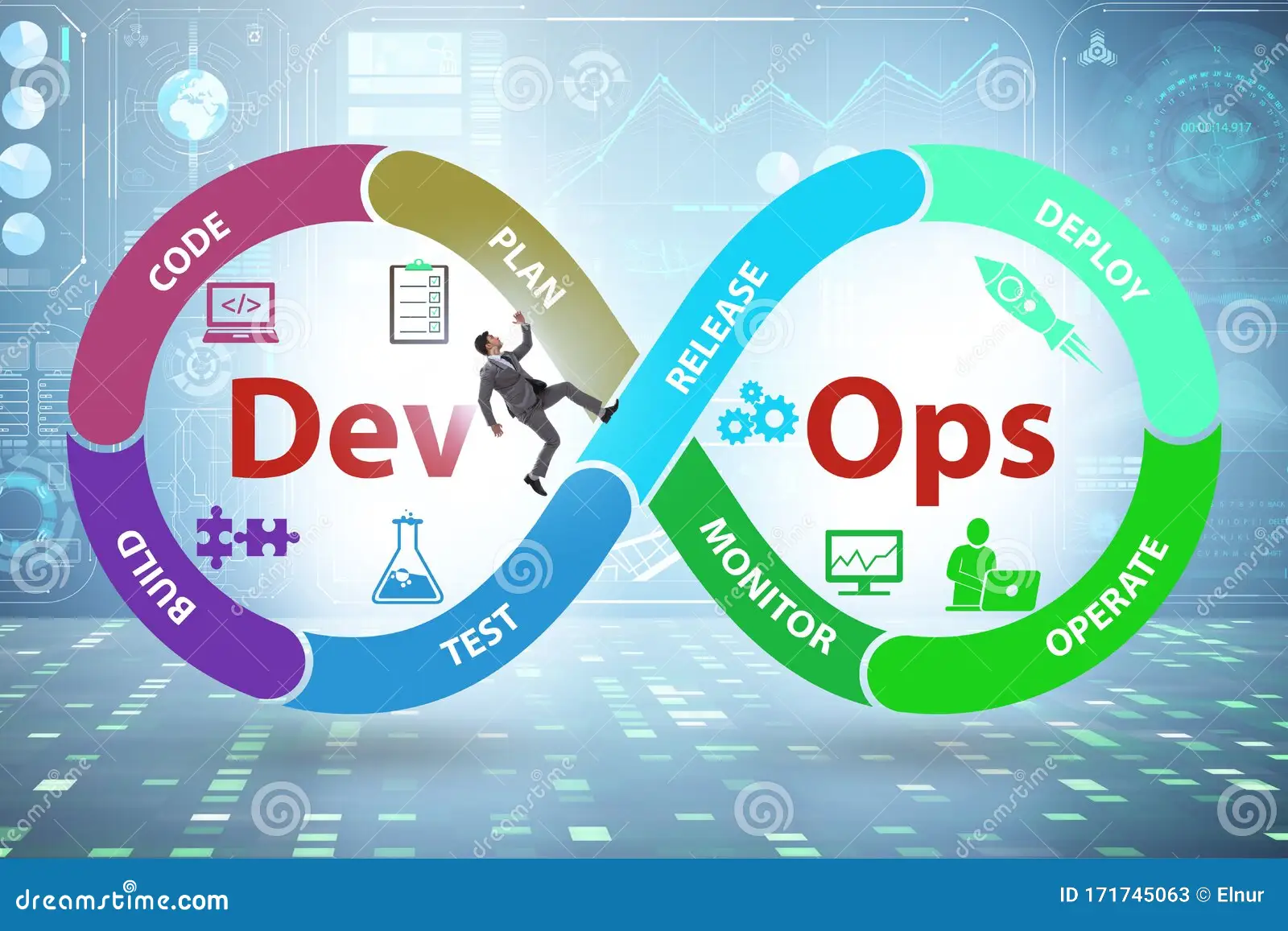
Integrate development and operations practices to automate workflows, enhance collaboration, and deliver software efficiently using CI/CD, monitoring, and infrastructure as code.

Leverage Amazon Web Services to build, deploy, and scale applications in the cloud with services for computing, storage, and security.

A versatile, object-oriented programming language used to build platform-independent applications, from enterprise solutions to mobile apps.

A powerful, low-level programming language known for its speed, efficiency, and control over hardware.

An extension of C that supports object-oriented, procedural, and generic programming.

A standard language for managing and manipulating relational databases.

Guiding your path to success
We provide continuous assistance even after your training ends, helping you excel in your workplace. Whether you’re facing technical challenges or need guidance on project tasks, our experts are here to support you.
Get help for issues you encounter at work
Improve your code for better performance.
Expert advice on your ongoing work assignments
Quick refreshers on course concepts when needed.
Assistance as per your work schedule.

Lightening up your future from DARK
Our internship program is designed to bridge the gap between academic learning and real-world industry experience. Whether you’re a fresher or a career switcher, we provide you with hands-on training, live projects, and mentorship from industry professionals.
Apply your classroom knowledge to solve real business challenges.
Work on live projects in your chosen domain.
Receive guidance from experts to sharpen your skills.
Gain a recognized certificate to boost your career profile.
Get tips and advice to prepare for your job interviews.
Fun, hands-on coding classes that build logic, creativity, and problem-solving— designed for young minds and absolute beginners.

Scratch games, animations, basic logic.
Scratch → Python, web basics, puzzles.
Python/JS apps, HTML/CSS, algorithms.
Build & present a project portfolio.
Prepare with real interview questions from top companies — click to reveal answers.
Feel free to contact us for any inquiries:
No 15, Nehru Street, Bhuvaneshwari Amman Nagar, Thailavaram, Guduvancheri
+91 8925148770
info@provigo.in
Learn the step-by-step process to become a full stack developer in the current job market.
Read MoreUnderstand the differences between these two career paths and choose what's best for you.
Read MoreDiscover the most useful Python libraries that every beginner should learn in 2024.
Read More"The Python training at provigo completely transformed my career. I got placed in a top MNC with a 100% salary hike."
"The hands-on approach and placement assistance helped me secure my dream job as a Full Stack Developer."
"Best institute in Chennai for data science training. The instructors are industry experts with real-world experience."